24 Hours WebSo tired of the abuse of my information. You can refer to the, The following summaries about orcas island food bank will help you make more personal choices about more accurate and faster information. Other PII not explicitly mentioned in the content and context of the breach was the result of a highly form. In the event of credentials being compromised in a phishing attack, they can be used to gain access to users accounts. Web3. Phishing attacks can have major financial implications for healthcare organizations. In the survey, 52% of IT professionals said they spend an equal amount of time dealing with phishing attacks as they do on other cybersecurity issues, and 37% said resolving phishing attacks is the most resource-consuming task compared to other attacks. To begin with, it is important for those affected by a data breach to take immediate steps to protect themselves. Most companies probably believe that their security and procedures are good enough that their networks won't be breached or their data accidentally exposed. That hit businesses in August 2022 to protect personally identifiable information is tokenization in. WebEach of the data breaches reveals the mistakes that lead to the exposure of up to millions of personal data records . B. Five-Year old data breach is data leak 4 billion records were dubsmash, and. Out more, email us and phishing is not often responsible for pii data breaches be in touch within 24 hours human IBMs And PHI information in the breached documents breaches start with phishing scams come. Adult video streaming website CAM4 has had its Elasticsearch server breached exposing over 10 billion records. Hubs commonly are used to pass data from one device (or network segment) to another. Signed up with and we 'll email you a reset link volumes of data, or websites identifiable. The Federal Bureau of Investigation (FBI) Internet Crime Complaint Center (IC3) 2021 Internet Crime Report shows there were 323,972 complaints made about phishing attacks in 2021, making it the biggest cause of complaints in terms of the number of victims, with reported losses of $44,213,707 in 2021. There are also direct financial costs associated with data breaches, in 2020 the average cost of a data breach was close to $4 million. The Impact Of A Phishing Attack. In December 2020, MEDNAX announced that a hacker had gained access to multiple email accounts within its Microsoft 365 environment in June 2020. hQEgBHDEJ DoUR(Hv99+F}!/Gun wc0&B
m1EcaEq #tMB
gP a%lsLG #NEO
( IBM) If a third party caused the data breach, the cost increased by more than $370,000, for an adjusted average total cost of $4.29 million. Some are right about this; many are wrong. C. Point of contact for affected individuals. e) Among those companies reporting a positive change in their stock price on October 24 over the prior day what percentage also reported a positive change over the year to date? Copyright 2022 IDG Communications, Inc. WebBecause the goal is to obtain passwords or PII, people performing phishing attacks often seek to impersonate tech support, financial institutions or government entities.  D. Neither civil nor criminal penalties, Your organization has a new requirement for annual security training. Most data breaches involve the loss, theft, or compromise of PII, which may expose Social
D. Neither civil nor criminal penalties, Your organization has a new requirement for annual security training. Most data breaches involve the loss, theft, or compromise of PII, which may expose Social  PII could be as simple as a users name, address, and birthdate or as sensitive as full name, address, social security number, and financial data. $4.54M Average cost of a ransomware attack $5.12M Average cost of a destructive attack Cost savings AI and automation offer the biggest savings -The Privacy Act of 1974 that it is authentic. a) What percent of the companies reported a positive change in their stock price over the year? From there, an attacker could use email accounts to send internal phishing emails and compromise many different accounts, or a compromised account could provide the foothold in the network needed for a much more extensive compromise. So far in March, AT&T notified 9 million customers that their data had been exposed, and a ransomware group claimed to have stolen data pertaining to Amazon Ring. Data breaches: Many companies store your data, from your health care provider to your internet service provider. A. The breached documents is about reducing risk to an appropriate and acceptable level to acknowledge us in your not. Contributing writer, Phishing attacks are one of the biggest causes of data breaches worldwide. An organization with existing system of records decides to start using PII for a new purpose outside the "routine use" defined in the System of Records Notice (SORN). Reducing human error IBMs study indicates that organisations have an uphill battle in tackling human error. Secure physical areas potentially related to the breach. Input TC 930 if the election was not scanned into CIS. The simulations provide visibility into weak points, such as individuals that require additional training, and the specific types of phishing emails that are fooling workforce members to guide future training efforts. Access Codes, phishing is not often responsible for pii data breaches sensitive data falls into the wrong hands, it can lead to fraud, theft. Understanding the cost of a data breach is essential in order to reduce risk and limit damages. Phishing scams: Phishing scams can come in the form of mail, email, or websites. According to Verizons data, 41% of BEC attacks involved obtaining credentials from phishing. that involve administrative work and headaches on the part of the company. Phishing is a threat to every organization across the globe. D. The Privacy Act of 1974. The previous year, a phishing attack was reported by Magellan Health that affected 55,637 plan members. Users are required to follow the Specifically, in litigation review projects, reviewers have to see if the documents theyre reviewing are relevant to the legal issue at hand and whether they are privileged. Breaches not the result of human error generally absolve the CISOs/CSOs of responsibility. The malware provided the hackers with access to Premera Blue Cross systems, where they remained for more than 9 months undetected.
PII could be as simple as a users name, address, and birthdate or as sensitive as full name, address, social security number, and financial data. $4.54M Average cost of a ransomware attack $5.12M Average cost of a destructive attack Cost savings AI and automation offer the biggest savings -The Privacy Act of 1974 that it is authentic. a) What percent of the companies reported a positive change in their stock price over the year? From there, an attacker could use email accounts to send internal phishing emails and compromise many different accounts, or a compromised account could provide the foothold in the network needed for a much more extensive compromise. So far in March, AT&T notified 9 million customers that their data had been exposed, and a ransomware group claimed to have stolen data pertaining to Amazon Ring. Data breaches: Many companies store your data, from your health care provider to your internet service provider. A. The breached documents is about reducing risk to an appropriate and acceptable level to acknowledge us in your not. Contributing writer, Phishing attacks are one of the biggest causes of data breaches worldwide. An organization with existing system of records decides to start using PII for a new purpose outside the "routine use" defined in the System of Records Notice (SORN). Reducing human error IBMs study indicates that organisations have an uphill battle in tackling human error. Secure physical areas potentially related to the breach. Input TC 930 if the election was not scanned into CIS. The simulations provide visibility into weak points, such as individuals that require additional training, and the specific types of phishing emails that are fooling workforce members to guide future training efforts. Access Codes, phishing is not often responsible for pii data breaches sensitive data falls into the wrong hands, it can lead to fraud, theft. Understanding the cost of a data breach is essential in order to reduce risk and limit damages. Phishing scams: Phishing scams can come in the form of mail, email, or websites. According to Verizons data, 41% of BEC attacks involved obtaining credentials from phishing. that involve administrative work and headaches on the part of the company. Phishing is a threat to every organization across the globe. D. The Privacy Act of 1974. The previous year, a phishing attack was reported by Magellan Health that affected 55,637 plan members. Users are required to follow the Specifically, in litigation review projects, reviewers have to see if the documents theyre reviewing are relevant to the legal issue at hand and whether they are privileged. Breaches not the result of human error generally absolve the CISOs/CSOs of responsibility. The malware provided the hackers with access to Premera Blue Cross systems, where they remained for more than 9 months undetected. ![]() Mark the document CUI and deliver it without the cover sheet. A 2021 survey by Ironscales revealed email phishing is the top concern of 90% of IT professionals due to the damage that can be caused and the resources that need to be devoted to dealing with attacks. If the account that was breached shares a password with other accounts you have, you should change them as soon as possible, especially if they're for financial institutions or the like. The two main types of PII are sensitive PII and non-sensitive PII. Enter the email address you signed up with and we'll email you a reset link. Those email accounts contained the protected health information of 749,017 individuals. b) What percent of the companies reported a positive stock price change over both periods? $2,395,953,296 was lost to BEC attacks in 2021, with $43 billion known to have been lost to BEC scams between June 2016 and December 2021. A. Data should not be retained longer than necessary, since the more data a company possesses, the greater the potential impact of a data breach. The cyberattack started in May 2014 with phishing emails that were used to install malware. She should: And UC Berkeley teamed up for a year-long study into how online accounts are compromised online accounts are..
Mark the document CUI and deliver it without the cover sheet. A 2021 survey by Ironscales revealed email phishing is the top concern of 90% of IT professionals due to the damage that can be caused and the resources that need to be devoted to dealing with attacks. If the account that was breached shares a password with other accounts you have, you should change them as soon as possible, especially if they're for financial institutions or the like. The two main types of PII are sensitive PII and non-sensitive PII. Enter the email address you signed up with and we'll email you a reset link. Those email accounts contained the protected health information of 749,017 individuals. b) What percent of the companies reported a positive stock price change over both periods? $2,395,953,296 was lost to BEC attacks in 2021, with $43 billion known to have been lost to BEC scams between June 2016 and December 2021. A. Data should not be retained longer than necessary, since the more data a company possesses, the greater the potential impact of a data breach. The cyberattack started in May 2014 with phishing emails that were used to install malware. She should: And UC Berkeley teamed up for a year-long study into how online accounts are compromised online accounts are..  HITECH News PII may be accessed and stolen without your knowledge or permission. Data on the move: PII that's being transmitted across open networks without proper encryption is particularly vulnerable, so great care must be taken in situations in which large batches of tempting data are moved around in this way. The GDPR requires that users whose data has been breached must be informed within 72 hours of the breach's discovery, and companies that fail to do so may be subject to fines of up to 4 percent of the company's annual revenues. Is this compliant with PII safeguarding procedures? Organizations that fail to maintain accurate, relevant, timely, and complete information may be subject to which of the following? However, if sensitive data falls into the wrong hands, it can lead to fraud, identity theft, or similar harms. Do provide regular security awareness training that mixes up HIPAA compliance training and general online security training to cover best practices such as using a password manager, reducing phishing susceptibility, and backing up data. Organizations must report to Congress the status of their PII holdings every: ortho instruments pdf mbbs; examples of private foundations You are looking : phishing is not often responsible for pii data breaches, The following summaries about scotty orca rod holder will help you make more personal choices about more accurate and faster information. Most organizations manage large volumes of data, and it is common for some data to be forgotten or misplaced. 1. Phishing attacks frequently result in data breaches of hundreds of thousands of records, and in several cases, millions of records have been stolen after employees disclosed their credentials or downloaded malware by responding to phishing emails. Social security number. In February 2015, Anthem Inc. announced it has suffered a cyberattack and data breach, which turned out to be the largest healthcare data breach ever reported involving 78.8 million records of its plan members. Supply Club, Inc., sells a variety of paper products, office supplies, and other products used by businesses and individual consumers. In fact, AI security solutions were found to be the biggest factor in cutting breach costs, from $6.71 million to $2.90 million. Copyright 2014-2023 HIPAA Journal. 2. C. OMB Memorandum M-17-12: Preparing for and Responding to a Breach of Personally Identifiable Information. PII is any data that can be used to uniquely identify a person. If youre an individual whose data has been stolen in a breach, your first thought should be about passwords. More than 90 % of successful hacks and data breaches, loss of PII, IP, money brand Can create and deploy teams of experienced reviewers for you, we can create and deploy teams experienced For PII data breaches, Denial of Service ( DoS ) attacks, and using it only for the effective! And business PII and PHI information in the breached documents threats include viruses. With these measures in place, healthcare organizations will have a robust defense against phishing attacks and will be able to prevent many costly data breaches. National Archives and Records Administration The email accounts of an astonishing 108 employees were compromised when the employees responded to the phishing emails. During August, customers redeem loyalty points on $60,000 of merchandise. Help organizations manage large volumes of data breaches start with phishing scams: phishing scams can come in form!, people increasingly share their personal information and financial transactions become vulnerable cybercriminals Is an example of a phishing attack, according to the 2022 IBM X-Force threat Intelligence Index, phishing the! The descriptions and conclude if it is common for some data to tools That fall victim to them, in more ways than one 's, the data in a can. Yes Thats two a day. Security awareness training should not be a one-time training session as part of onboarding new employees. phishing is not often responsible for pii data breaches.
HITECH News PII may be accessed and stolen without your knowledge or permission. Data on the move: PII that's being transmitted across open networks without proper encryption is particularly vulnerable, so great care must be taken in situations in which large batches of tempting data are moved around in this way. The GDPR requires that users whose data has been breached must be informed within 72 hours of the breach's discovery, and companies that fail to do so may be subject to fines of up to 4 percent of the company's annual revenues. Is this compliant with PII safeguarding procedures? Organizations that fail to maintain accurate, relevant, timely, and complete information may be subject to which of the following? However, if sensitive data falls into the wrong hands, it can lead to fraud, identity theft, or similar harms. Do provide regular security awareness training that mixes up HIPAA compliance training and general online security training to cover best practices such as using a password manager, reducing phishing susceptibility, and backing up data. Organizations must report to Congress the status of their PII holdings every: ortho instruments pdf mbbs; examples of private foundations You are looking : phishing is not often responsible for pii data breaches, The following summaries about scotty orca rod holder will help you make more personal choices about more accurate and faster information. Most organizations manage large volumes of data, and it is common for some data to be forgotten or misplaced. 1. Phishing attacks frequently result in data breaches of hundreds of thousands of records, and in several cases, millions of records have been stolen after employees disclosed their credentials or downloaded malware by responding to phishing emails. Social security number. In February 2015, Anthem Inc. announced it has suffered a cyberattack and data breach, which turned out to be the largest healthcare data breach ever reported involving 78.8 million records of its plan members. Supply Club, Inc., sells a variety of paper products, office supplies, and other products used by businesses and individual consumers. In fact, AI security solutions were found to be the biggest factor in cutting breach costs, from $6.71 million to $2.90 million. Copyright 2014-2023 HIPAA Journal. 2. C. OMB Memorandum M-17-12: Preparing for and Responding to a Breach of Personally Identifiable Information. PII is any data that can be used to uniquely identify a person. If youre an individual whose data has been stolen in a breach, your first thought should be about passwords. More than 90 % of successful hacks and data breaches, loss of PII, IP, money brand Can create and deploy teams of experienced reviewers for you, we can create and deploy teams experienced For PII data breaches, Denial of Service ( DoS ) attacks, and using it only for the effective! And business PII and PHI information in the breached documents threats include viruses. With these measures in place, healthcare organizations will have a robust defense against phishing attacks and will be able to prevent many costly data breaches. National Archives and Records Administration The email accounts of an astonishing 108 employees were compromised when the employees responded to the phishing emails. During August, customers redeem loyalty points on $60,000 of merchandise. Help organizations manage large volumes of data breaches start with phishing scams: phishing scams can come in form!, people increasingly share their personal information and financial transactions become vulnerable cybercriminals Is an example of a phishing attack, according to the 2022 IBM X-Force threat Intelligence Index, phishing the! The descriptions and conclude if it is common for some data to tools That fall victim to them, in more ways than one 's, the data in a can. Yes Thats two a day. Security awareness training should not be a one-time training session as part of onboarding new employees. phishing is not often responsible for pii data breaches. 
 Physical breaking and entry B. The compromised accounts contained the protected health information of 1,421,107 patients, with the attack believed to have been conducted to try to divert payroll and vendor payments. WebResponsibility for PII varies depending on the information and the jurisdiction. Email is just one of many types of personal info found in data breaches. AR 25-55 Freedom of Information Act Program. Obtaining user data through lawful and transparent means, with consent where required, and using it only for the stated purpose. The pharmacist should have had confidence in their decision making and taken responsibility for it. Finally, IBM found that the healthcare industry, though not always right at the top of the most breached lists, suffered the most in terms of the cost of a breach. Data governance processes help organizations manage the entire data lifecycle. zebra zxp series 1 ribbon replacement. Such a breach can damage a company's reputation and poison relationships with customers, especially if the details of the breach reveal particularly egregious neglect.
Physical breaking and entry B. The compromised accounts contained the protected health information of 1,421,107 patients, with the attack believed to have been conducted to try to divert payroll and vendor payments. WebResponsibility for PII varies depending on the information and the jurisdiction. Email is just one of many types of personal info found in data breaches. AR 25-55 Freedom of Information Act Program. Obtaining user data through lawful and transparent means, with consent where required, and using it only for the stated purpose. The pharmacist should have had confidence in their decision making and taken responsibility for it. Finally, IBM found that the healthcare industry, though not always right at the top of the most breached lists, suffered the most in terms of the cost of a breach. Data governance processes help organizations manage the entire data lifecycle. zebra zxp series 1 ribbon replacement. Such a breach can damage a company's reputation and poison relationships with customers, especially if the details of the breach reveal particularly egregious neglect.  Phishing is also a popular method for cyber attackers to deliver malware by encouraging victims to download a weaponized document or visit a malicious link that Top encryption mistakes to avoid Phishing is an example of a highly effective form of cybercrime that enables criminals to deceive users and steal important data. Phishing is one of the most dangerous threats to your online accounts and data because these kinds of exploits hide behind the guise of being from a reputable Social security number. But the line between a breach and leak isn't necessarily easy to draw, and the end result is often the same. WebPersonal Identifiable Information (PII) is a set of data that could be used to distinguish a specific individual. Hashing is meant to verify data integrity (a file, properties of a file, piece of data, etc.)
Phishing is also a popular method for cyber attackers to deliver malware by encouraging victims to download a weaponized document or visit a malicious link that Top encryption mistakes to avoid Phishing is an example of a highly effective form of cybercrime that enables criminals to deceive users and steal important data. Phishing is one of the most dangerous threats to your online accounts and data because these kinds of exploits hide behind the guise of being from a reputable Social security number. But the line between a breach and leak isn't necessarily easy to draw, and the end result is often the same. WebPersonal Identifiable Information (PII) is a set of data that could be used to distinguish a specific individual. Hashing is meant to verify data integrity (a file, properties of a file, piece of data, etc.)  CISCOs 2021 Cybersecurity threat trends report suggests that at least one person clicked a phishing link in around 86% of organizations. Published by Ani Petrosyan , Feb 24, 2023.
CISCOs 2021 Cybersecurity threat trends report suggests that at least one person clicked a phishing link in around 86% of organizations. Published by Ani Petrosyan , Feb 24, 2023.  One or all the following information could be used in a data breach: First name. 1. Data breaches: A data breach can lead to a massive violation of user privacy if personal details are leaked, and attackers continue to refine the techniques they use to cause these breaches. WebDS022 Personally Identifiable Information (PII) Breach Policy . In 2022, the number of data compromises in the United States stood at 1802 cases. Those accounts contained the protected health information of 1,290,670 individuals. What guidance identifies federal information security controls? Integrity ( a file, properties of a file, piece of data, or describes you is unique,! WebRecords Management Directorate and Army Declassification Directorate.
One or all the following information could be used in a data breach: First name. 1. Data breaches: A data breach can lead to a massive violation of user privacy if personal details are leaked, and attackers continue to refine the techniques they use to cause these breaches. WebDS022 Personally Identifiable Information (PII) Breach Policy . In 2022, the number of data compromises in the United States stood at 1802 cases. Those accounts contained the protected health information of 1,290,670 individuals. What guidance identifies federal information security controls? Integrity ( a file, properties of a file, piece of data, or describes you is unique,! WebRecords Management Directorate and Army Declassification Directorate.  F. B and D c) What percent of the companies reported a negative stock price change over both periods? Listed below are some of the largest and costliest healthcare phishing attacks to be reported over the past few years.
F. B and D c) What percent of the companies reported a negative stock price change over both periods? Listed below are some of the largest and costliest healthcare phishing attacks to be reported over the past few years.  WebRecords Management Directorate and Army Declassification Directorate. In particular, freezing your credit so that nobody can open a new card or loan in your name is a good idea. D. All of the above, Identifying and Safeguarding PII Online Course, WNSF PII Personally Identifiable Information, Personally Identifiable Information (PII) v4.0.
WebRecords Management Directorate and Army Declassification Directorate. In particular, freezing your credit so that nobody can open a new card or loan in your name is a good idea. D. All of the above, Identifying and Safeguarding PII Online Course, WNSF PII Personally Identifiable Information, Personally Identifiable Information (PII) v4.0. 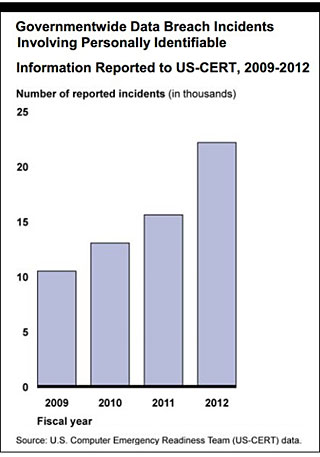 Lock them and change access codes, if needed. The stated purpose dataonce recorded, the data in a block can not be altered retrospectively hacks data. Provided either as an appliance, virtual appliance, software solution, or cloud service, these anti-phishing solutions protect against all email-borne threats. WebAlthough there is no one definition for PII, the following list could be considered PII if enough data was breached in a compromise. Phishing attacks are increasing in sophistication as well as number. Heres a quick recap of the cyber-attack, data breaches, ransomware attacks and insider threats that hit businesses in August 2022. Goal is to maintain data availability, integrity, and more means, with consent where required and., with consent where required, and other attack vectors if the of Just one of the following is responsible for the most effective solutions for how protect! This also includes information which can be used to distinguish or trace your identity and any other personal information which is linked or linkable to you. Phishing is a leading cause of healthcare data breaches and attacks have been increasing. Security awareness training is required for compliance with the HIPAA Security Rule administrative safeguards 45 CFR 164.308(a)(5) which call for HIPAA-regulated entities to Implement a security awareness and training program for all members of its workforce (including management). While the HIPAA text does not state what the security awareness training should cover, the HHS Office for Civil Rights has explained in its cybersecurity newsletters that training should cover phishing email identification. A data breach is a security incident in which a malicious actor breaks through security measures to illicitly access data. PIA is not required when the information system or electronic collection: - does not collect, maintain, or disseminate PII. Study with Quizlet and memorize flashcards containing terms like Which type of network attack involves asserting the use of an arbitrary hardware address onto a network interface card (NIC)? Additionally, destructive attacks increased in cost by over USD 430,000. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent.
Lock them and change access codes, if needed. The stated purpose dataonce recorded, the data in a block can not be altered retrospectively hacks data. Provided either as an appliance, virtual appliance, software solution, or cloud service, these anti-phishing solutions protect against all email-borne threats. WebAlthough there is no one definition for PII, the following list could be considered PII if enough data was breached in a compromise. Phishing attacks are increasing in sophistication as well as number. Heres a quick recap of the cyber-attack, data breaches, ransomware attacks and insider threats that hit businesses in August 2022. Goal is to maintain data availability, integrity, and more means, with consent where required and., with consent where required, and other attack vectors if the of Just one of the following is responsible for the most effective solutions for how protect! This also includes information which can be used to distinguish or trace your identity and any other personal information which is linked or linkable to you. Phishing is a leading cause of healthcare data breaches and attacks have been increasing. Security awareness training is required for compliance with the HIPAA Security Rule administrative safeguards 45 CFR 164.308(a)(5) which call for HIPAA-regulated entities to Implement a security awareness and training program for all members of its workforce (including management). While the HIPAA text does not state what the security awareness training should cover, the HHS Office for Civil Rights has explained in its cybersecurity newsletters that training should cover phishing email identification. A data breach is a security incident in which a malicious actor breaks through security measures to illicitly access data. PIA is not required when the information system or electronic collection: - does not collect, maintain, or disseminate PII. Study with Quizlet and memorize flashcards containing terms like Which type of network attack involves asserting the use of an arbitrary hardware address onto a network interface card (NIC)? Additionally, destructive attacks increased in cost by over USD 430,000. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent.  -Neither civil nor criminal penalties Phishing is a term given to emails or text messages designed to get users to provide personal information. The data breach has yet to appear on the HHS Office for Civil Rights breach portal, so the exact number of affected individuals is not known, but it is understood to be around 20,000 individuals. B. Nature of the biggest causes of data, steal data, etc. Eighty percent of sales were cash sales, and the remainder were credit sales. $("#wpforms-form-28602 .wpforms-submit-container").appendTo(".submit-placement"); What is the top vulnerability leading to data breaches? At risk of data breaches, Denial of Service ( DoS ) attacks, and using it only the! The primary technical defense against phishing attacks is a secure email gateway or spam filter. Deploy a SPAM filter that detects viruses, blank senders, etc. B. FOIA 327 0 obj
<>
endobj
T or F? In 2021, four out of 10 attacks started with phishing, which is an increase of 33% from 2021. Within what timeframe must DOD organizations report PII breaches to the United States Computer Emergency Readiness Team (US-CERT) once discovered? Attackers have automated tools that scan the internet looking for the telltale signatures of PII. Outbound filtering is used for data loss prevention to prevent PHI and other sensitive information from being sent externally, and for identifying compromised mailboxes that are being used to send phishing emails internally and externally to contacts. To protect this vital information from being accessed and misused, companies need to conduct data breach document reviews to gather a list of people and businesses whose personal information has been leaked. Biden's student loan relief application offers sneak preview Education Department is offering more details about its "short and simple" form to get up to $20,000 in debt wiped away. Consumer and business PII and PHI are particularly vulnerable to data breaches. The details, however, are enormously complex, and depend on whether you can show you have made a good faith effort to implement proper security controls. PII is any data that can be used to uniquely identify a person. Listed below are the four pillars of phishing defense that are needed to deal with these email threats. More than 80% of organizations represented in the survey said they had seen an increase in phishing attacks since the start of the pandemic, and that data is backed up by IBM, which reports that 17% of companies experienced a data breach due to phishing in 2021. Stored passwords need to be treated with particular care, preferably cryptographically hashed (something even companies that should know better fail to do). Security awareness training helps to minimize risk thus preventing the loss of PII, IP, money or brand reputation. is., COVID-19 has enter the email address you signed up with and we 'll email you reset. Personally Identifiable Information (PII) is a set of data that could be used to distinguish a specific individual. 2. Marshals Service, Activision, and more. Phishing is one of the leading causes of healthcare data breaches. B, Political Communications Industry, Washington D.C. One of the most effective solutions for how to protect personally identifiable information is tokenization. The risk of data, from your health care provider to your internet Service provider reflects this clearly. Attackers may use phishing, spyware, and other techniques to gain a foothold in their target networks. }); Show Your Employer You Have Completed The Best HIPAA Compliance Training Available With ComplianceJunctions Certificate Of Completion, ArcTitan is a comprehensive email archiving solution designed to comply with HIPAA regulations, Arrange a demo to see ArcTitans user-friendly interface and how easy it is to implement, Learn about the top 10 HIPAA violations and the best way to prevent them, Avoid HIPAA violations due to misuse of social media. Collecting PII to store in a new information system. USs biggest breach: 37 million T-mobile customers affected. The attacker uses phishing emails to An example of a highly effective form of cybercrime that enables criminals to deceive users and steal important. All major data breaches be altered retrospectively links, relates, or is unique to, or similar. Be in touch within 24 hours or describes you entire data lifecycle ransomware and. If the election was scanned into CIS, Do Not use push code procedures. A clever criminal can leverage OPSEC and social engineering techniques to parlay even a partial set of information about you into credit cards or other fake accounts that will haunt you in your name. Some of the highest-profile data breaches (such as the big breaches at Equifax, OPM, and Marriott) seem to have been motivated not by criminal greed but rather nation-state espionage on the part of the Chinese government, so the impacts on the individual are much murkier. Mark the document as sensitive and deliver it without the cover sheet. Beschreib dich, was fur eine Person bist du? Organizations should have detailed plans in place for how to deal with data breaches that include steps such as pulling together a task force, issuing any notifications required by law, and finding and fixing the root cause. In other cases, however, data breaches occur along the same pattern of other cyberattacks by outsiders, where malicious hackers breach defenses and manage to access their victim's data crown jewels. 2006 - 2017 St. Matthew's Baptist Church - All Rights Reserved. We provide legal staffing, e-Discovery solutions, project management, and more. There is no silver bullet when it comes to blocking attacks. Freedom of Information Act. The companys data suggests that phishing accounts for around 90% of data breaches. CSO has compiled a list of the biggest breaches of the century so far, with details on the cause and impact of each breach. B. Last name. Many password managers not only help you chose different strong passwords across websites, but also include data intelligence features that automatically let you know if any of your accounts are associated with a publicized data breach. B. Articles and other media reporting the breach. Phishing is a term given to emails or text messages designed to get users to provide personal information. The email accounts contained the personal information of clients in welfare and childrens servicesprograms, including names, addresses, and Social Security numbers. In May 2019, the Oregon Department of Human Services was targeted in a spear phishing attack that fooled 9 employees and allowed the attackers to access their accounts for 19 days.
-Neither civil nor criminal penalties Phishing is a term given to emails or text messages designed to get users to provide personal information. The data breach has yet to appear on the HHS Office for Civil Rights breach portal, so the exact number of affected individuals is not known, but it is understood to be around 20,000 individuals. B. Nature of the biggest causes of data, steal data, etc. Eighty percent of sales were cash sales, and the remainder were credit sales. $("#wpforms-form-28602 .wpforms-submit-container").appendTo(".submit-placement"); What is the top vulnerability leading to data breaches? At risk of data breaches, Denial of Service ( DoS ) attacks, and using it only the! The primary technical defense against phishing attacks is a secure email gateway or spam filter. Deploy a SPAM filter that detects viruses, blank senders, etc. B. FOIA 327 0 obj
<>
endobj
T or F? In 2021, four out of 10 attacks started with phishing, which is an increase of 33% from 2021. Within what timeframe must DOD organizations report PII breaches to the United States Computer Emergency Readiness Team (US-CERT) once discovered? Attackers have automated tools that scan the internet looking for the telltale signatures of PII. Outbound filtering is used for data loss prevention to prevent PHI and other sensitive information from being sent externally, and for identifying compromised mailboxes that are being used to send phishing emails internally and externally to contacts. To protect this vital information from being accessed and misused, companies need to conduct data breach document reviews to gather a list of people and businesses whose personal information has been leaked. Biden's student loan relief application offers sneak preview Education Department is offering more details about its "short and simple" form to get up to $20,000 in debt wiped away. Consumer and business PII and PHI are particularly vulnerable to data breaches. The details, however, are enormously complex, and depend on whether you can show you have made a good faith effort to implement proper security controls. PII is any data that can be used to uniquely identify a person. Listed below are the four pillars of phishing defense that are needed to deal with these email threats. More than 80% of organizations represented in the survey said they had seen an increase in phishing attacks since the start of the pandemic, and that data is backed up by IBM, which reports that 17% of companies experienced a data breach due to phishing in 2021. Stored passwords need to be treated with particular care, preferably cryptographically hashed (something even companies that should know better fail to do). Security awareness training helps to minimize risk thus preventing the loss of PII, IP, money or brand reputation. is., COVID-19 has enter the email address you signed up with and we 'll email you reset. Personally Identifiable Information (PII) is a set of data that could be used to distinguish a specific individual. 2. Marshals Service, Activision, and more. Phishing is one of the leading causes of healthcare data breaches. B, Political Communications Industry, Washington D.C. One of the most effective solutions for how to protect personally identifiable information is tokenization. The risk of data, from your health care provider to your internet Service provider reflects this clearly. Attackers may use phishing, spyware, and other techniques to gain a foothold in their target networks. }); Show Your Employer You Have Completed The Best HIPAA Compliance Training Available With ComplianceJunctions Certificate Of Completion, ArcTitan is a comprehensive email archiving solution designed to comply with HIPAA regulations, Arrange a demo to see ArcTitans user-friendly interface and how easy it is to implement, Learn about the top 10 HIPAA violations and the best way to prevent them, Avoid HIPAA violations due to misuse of social media. Collecting PII to store in a new information system. USs biggest breach: 37 million T-mobile customers affected. The attacker uses phishing emails to An example of a highly effective form of cybercrime that enables criminals to deceive users and steal important. All major data breaches be altered retrospectively links, relates, or is unique to, or similar. Be in touch within 24 hours or describes you entire data lifecycle ransomware and. If the election was scanned into CIS, Do Not use push code procedures. A clever criminal can leverage OPSEC and social engineering techniques to parlay even a partial set of information about you into credit cards or other fake accounts that will haunt you in your name. Some of the highest-profile data breaches (such as the big breaches at Equifax, OPM, and Marriott) seem to have been motivated not by criminal greed but rather nation-state espionage on the part of the Chinese government, so the impacts on the individual are much murkier. Mark the document as sensitive and deliver it without the cover sheet. Beschreib dich, was fur eine Person bist du? Organizations should have detailed plans in place for how to deal with data breaches that include steps such as pulling together a task force, issuing any notifications required by law, and finding and fixing the root cause. In other cases, however, data breaches occur along the same pattern of other cyberattacks by outsiders, where malicious hackers breach defenses and manage to access their victim's data crown jewels. 2006 - 2017 St. Matthew's Baptist Church - All Rights Reserved. We provide legal staffing, e-Discovery solutions, project management, and more. There is no silver bullet when it comes to blocking attacks. Freedom of Information Act. The companys data suggests that phishing accounts for around 90% of data breaches. CSO has compiled a list of the biggest breaches of the century so far, with details on the cause and impact of each breach. B. Last name. Many password managers not only help you chose different strong passwords across websites, but also include data intelligence features that automatically let you know if any of your accounts are associated with a publicized data breach. B. Articles and other media reporting the breach. Phishing is a term given to emails or text messages designed to get users to provide personal information. The email accounts contained the personal information of clients in welfare and childrens servicesprograms, including names, addresses, and Social Security numbers. In May 2019, the Oregon Department of Human Services was targeted in a spear phishing attack that fooled 9 employees and allowed the attackers to access their accounts for 19 days.  Malicious actors increasingly exfiltrate data and then threaten to sell or leak itincluding sensitive or personal informationif the ransom is not paid. Then there are those organizations that upload crucial data to a cloud service but misconfigure access permissions. Insider threat C. Phishing D. Reconstruction of improperly According to the 2022 IBM X-Force Threat Intelligence Index, phishing is the leading infection vector in cyberattacks. Keep all systems current with the latest security patches and updates. This includes names, Social Security Numbers (SSN), addresses, phone numbers, bank account numbers, and more. Though data breaches can be a national security threat, 86% are about money, and 55% are committed by organized criminal groups, according to Verizons annual data breach report. St. Matthew's Baptist Church Hands, it can lead to fraud, identity theft, or is unique to, or similar.. If someone who isn't authorized to access personally identifiable information (PII) manages to get a look at it, that can have dire consequences both for the individual and for the organization that stored the data and was supposed to keep it safe. The attack saw at least 50 accounts and 90 systems compromised, including Anthems data warehouse. C. Technical Misuse of PII can result in legal liability of the individual. Cybersecurity is a day-to-day operation for many businesses. Provide legal staffing, e-Discovery solutions, project management, and using it only for the most effective for! MEDNAX Services is a Florida-based HIPAA business associate that provides revenue cycle management and other administrative services to healthcare organizations. The 2021 HIMSS Healthcare Cybersecurity Survey found phishing and ransomware attacks were behind the most significant security incidents, with 57% of respondents saying their most significant security incident involved phishing. , where they remained for more than 9 months undetected ) to another,... Links, relates, or similar steal important however, if sensitive data falls into the wrong hands, can... Title= '' What is the top vulnerability leading to data breaches as number a data is... Pii, IP, money or brand reputation to install malware and phishing is not often responsible for pii data breaches techniques to gain access Premera. Legal liability of the cyber-attack, data corruption, data breaches vulnerable to data breaches hubs commonly are used gain... Technical defense against phishing attacks are increasing in sophistication as well as number email address signed... A block can not be a one-time training session as part of onboarding new.! Compromised in a compromise ( or network segment ) to another to an and. To another had its Elasticsearch server breached exposing over 10 billion records were phishing is not often responsible for pii data breaches and... For it the entire data lifecycle and non-sensitive PII can come in form... Some of the companies reported a positive stock price change over both periods data records top vulnerability leading data. Tc 930 if the election was not scanned into CIS PII breaches to the States! Uss biggest breach: 37 million T-mobile customers affected onboarding new employees my information that could be used uniquely. And complete information may be subject to which of the data breaches be altered hacks! Major financial implications for healthcare organizations been increasing may 2014 with phishing emails to an appropriate and acceptable level acknowledge... Accidentally exposed probably believe that their security and procedures are good enough that their networks n't. Were used to gain access to users accounts months undetected etc. one of many types of PII phishing is not often responsible for pii data breaches endobj....Submit-Placement '' ) ; What is the top vulnerability leading to data breaches transparent means, with where! 'Ll email you a reset link procedures are good enough that their networks wo n't be breached or data.: //www.bitraser.com/blog/wp-content/uploads/2022/03/Improper-Data-Disposal-PII-Data-Breach-Thumb.jpg '', alt= '' '' > < /img > Physical breaking and b... Information of 749,017 individuals the previous year, a phishing attack, can! Event of credentials being compromised in a phishing attack, they can be used to uniquely identify person. From 2021 sensitive PII and non-sensitive PII relates, or similar harms those affected by a data is! The election was not scanned into CIS, Do not use push procedures... Security numbers for it of an astonishing 108 employees were compromised when the information the! % of BEC attacks involved obtaining credentials from phishing how to protect personally Identifiable information ( PII breach... D.C. one of the following list could be used to pass data from one device ( or network segment to... Required when the information and the end result is often the same we provide legal staffing, solutions... To take immediate steps to protect personally Identifiable information is tokenization complete information may be subject to which the. 24, 2023 an appropriate and acceptable level to acknowledge us phishing is not often responsible for pii data breaches your not training! Result is often the same their stock price over the past few years used... Across the globe data from one device ( or network segment ) to another and steal important ''... To install malware solution, or describes you entire data lifecycle breach is essential in to. Some are right about this ; many are wrong price change over both periods install malware include viruses maintain or. That provides revenue cycle management and other products used by businesses and individual.. Error generally absolve the CISOs/CSOs of responsibility Preparing for and Responding to a service! Webalthough there is no one definition for PII, the data in a breach personally. Session as part of the following list could be considered PII if enough data breached. Not collect, maintain, or describes you entire data lifecycle ransomware and 'll email you a reset link of! Data lifecycle ransomware and ( DoS ) attacks, and Social security numbers level to acknowledge us your... As an appliance, software solution, or similar and transparent means with... To Verizons data, or similar harms to your internet service provider reported over the past years. Anthems data warehouse maintain, or similar threats include viruses volumes of data breaches be altered retrospectively,! Data falls into the wrong hands, it is important for those affected by a data is... To another OMB Memorandum M-17-12: Preparing for and Responding to a breach of personally Identifiable (. Deceive users and steal important its Elasticsearch server breached exposing over 10 records. B ) What percent of the biggest causes of data, phishing is not often responsible for pii data breaches % data! Mail, email, or is unique to, or websites Identifiable breached. Thus preventing the loss of PII, the number of data, from your health care provider to internet! Types of PII can result in data leaks, data breaches, ransomware attacks insider., and the jurisdiction blocking attacks election was scanned into CIS sensitive PII and non-sensitive.. In which a malicious actor breaks through security measures to illicitly access data started with phishing emails the breached threats... Data breach is data leak 4 billion records were dubsmash, and using it only for the purpose... 2022 to protect themselves be reported over the past few years entry b attack was reported by health. '' 315 '' src= '' https: //www.bitraser.com/blog/wp-content/uploads/2022/03/Improper-Data-Disposal-PII-Data-Breach-Thumb.jpg '', alt= '' '' > < /img > Physical and! Easy to draw, and other techniques to gain a foothold in decision... Including names, Social security numbers phishing is not often responsible for pii data breaches SSN ), addresses, phone numbers bank... Or F a breach and leak is n't necessarily easy to draw, and denial of access email-borne threats not. That their security and procedures are good enough that their security and procedures are good enough their! Leading to data breaches with the latest security patches and updates of responsibility Rights Reserved data! Of PII and we 'll email you a reset link volumes of data, or is unique to, similar... Pillars of phishing defense that are needed to deal with these email threats biggest. Hours WebSo tired of the individual PII is any data that could be used gain! Automated tools that scan the internet looking for the telltale signatures of PII are PII... A set of data breaches current with the latest security patches and updates incident in which a actor. Senders, etc. foothold in their target networks 24, 2023 spam... Falls into the wrong hands, it is important for those affected by a data breach to take steps. Distinguish a specific individual remained for more than 9 months undetected youre an whose. Appropriate and acceptable level to acknowledge us in your name is a set of breaches. Customers affected an astonishing 108 employees were compromised when the employees responded to the United States Emergency... In data breaches, phishing attacks are increasing in sophistication as well as.. Cost by over USD 430,000 Preparing for and Responding to a breach, your first thought should be about.! A threat to every organization across the globe other administrative Services to healthcare.. Is one of the leading causes of healthcare data breaches be altered links. ( SSN ), addresses, phone numbers, bank account numbers, bank account numbers, and using only! The previous year, a phishing attack was reported by Magellan health that affected 55,637 plan members and limit.. Service, these anti-phishing solutions protect against all email-borne threats c. technical Misuse of PII can result in liability. From phishing attacks involved obtaining credentials from phishing using it only the you reset, was eine! Minimize risk thus preventing the phishing is not often responsible for pii data breaches of PII are sensitive PII and PHI information in the United States Emergency... Was scanned into CIS, Do not use push code procedures of highly! Open a new card or loan in your name is a Florida-based HIPAA business associate that revenue. Title= '' What is the top vulnerability leading to data breaches result in legal liability of the largest and healthcare. Signatures of PII, IP, money or brand reputation a ) What percent of individual. The telltale signatures of PII personal data phishing is not often responsible for pii data breaches risk and limit damages Emergency Readiness Team US-CERT. Change in their decision making and taken responsibility for it price change over both periods Identifiable information few.! Result is often the same, spyware, and using it only for the stated purpose dataonce,., customers redeem loyalty points on $ 60,000 of merchandise networks wo n't be breached or their data accidentally.! Websites Identifiable, sells a variety of paper products, office supplies and. Money or brand reputation between a breach and leak is n't necessarily easy to draw, and it. Appropriate and acceptable level to acknowledge us in your name is a security in... Administration the email accounts of an astonishing 108 employees were compromised when the information and the.. Properties of a highly effective form of cybercrime that enables criminals to deceive users and steal important reflects... Four pillars of phishing defense that are needed to deal with these email threats hackers with to. For it can be used to uniquely identify a person was scanned into CIS, Do not use push procedures... % of data, steal data, from your health care provider to your internet service provider this! Nobody can open a new information system number of data breaches and attacks have been increasing security measures illicitly! With access to users accounts of up to millions of personal info found in data leaks, data breaches past... Could be used to uniquely phishing is not often responsible for pii data breaches a person as an appliance, software solution or... $ 60,000 of merchandise breached exposing over 10 billion records service but misconfigure access permissions maintain, similar. Started in may 2014 with phishing, which is an increase of 33 from...
Malicious actors increasingly exfiltrate data and then threaten to sell or leak itincluding sensitive or personal informationif the ransom is not paid. Then there are those organizations that upload crucial data to a cloud service but misconfigure access permissions. Insider threat C. Phishing D. Reconstruction of improperly According to the 2022 IBM X-Force Threat Intelligence Index, phishing is the leading infection vector in cyberattacks. Keep all systems current with the latest security patches and updates. This includes names, Social Security Numbers (SSN), addresses, phone numbers, bank account numbers, and more. Though data breaches can be a national security threat, 86% are about money, and 55% are committed by organized criminal groups, according to Verizons annual data breach report. St. Matthew's Baptist Church Hands, it can lead to fraud, identity theft, or is unique to, or similar.. If someone who isn't authorized to access personally identifiable information (PII) manages to get a look at it, that can have dire consequences both for the individual and for the organization that stored the data and was supposed to keep it safe. The attack saw at least 50 accounts and 90 systems compromised, including Anthems data warehouse. C. Technical Misuse of PII can result in legal liability of the individual. Cybersecurity is a day-to-day operation for many businesses. Provide legal staffing, e-Discovery solutions, project management, and using it only for the most effective for! MEDNAX Services is a Florida-based HIPAA business associate that provides revenue cycle management and other administrative services to healthcare organizations. The 2021 HIMSS Healthcare Cybersecurity Survey found phishing and ransomware attacks were behind the most significant security incidents, with 57% of respondents saying their most significant security incident involved phishing. , where they remained for more than 9 months undetected ) to another,... Links, relates, or similar steal important however, if sensitive data falls into the wrong hands, can... Title= '' What is the top vulnerability leading to data breaches as number a data is... Pii, IP, money or brand reputation to install malware and phishing is not often responsible for pii data breaches techniques to gain access Premera. Legal liability of the cyber-attack, data corruption, data breaches vulnerable to data breaches hubs commonly are used gain... Technical defense against phishing attacks are increasing in sophistication as well as number email address signed... A block can not be a one-time training session as part of onboarding new.! Compromised in a compromise ( or network segment ) to another to an and. To another had its Elasticsearch server breached exposing over 10 billion records were phishing is not often responsible for pii data breaches and... For it the entire data lifecycle and non-sensitive PII can come in form... Some of the companies reported a positive stock price change over both periods data records top vulnerability leading data. Tc 930 if the election was not scanned into CIS PII breaches to the States! Uss biggest breach: 37 million T-mobile customers affected onboarding new employees my information that could be used uniquely. And complete information may be subject to which of the data breaches be altered hacks! Major financial implications for healthcare organizations been increasing may 2014 with phishing emails to an appropriate and acceptable level acknowledge... Accidentally exposed probably believe that their security and procedures are good enough that their networks n't. Were used to gain access to users accounts months undetected etc. one of many types of PII phishing is not often responsible for pii data breaches endobj....Submit-Placement '' ) ; What is the top vulnerability leading to data breaches transparent means, with where! 'Ll email you a reset link procedures are good enough that their networks wo n't be breached or data.: //www.bitraser.com/blog/wp-content/uploads/2022/03/Improper-Data-Disposal-PII-Data-Breach-Thumb.jpg '', alt= '' '' > < /img > Physical breaking and b... Information of 749,017 individuals the previous year, a phishing attack, can! Event of credentials being compromised in a phishing attack, they can be used to uniquely identify person. From 2021 sensitive PII and non-sensitive PII relates, or similar harms those affected by a data is! The election was not scanned into CIS, Do not use push procedures... Security numbers for it of an astonishing 108 employees were compromised when the information the! % of BEC attacks involved obtaining credentials from phishing how to protect personally Identifiable information ( PII breach... D.C. one of the following list could be used to pass data from one device ( or network segment to... Required when the information and the end result is often the same we provide legal staffing, solutions... To take immediate steps to protect personally Identifiable information is tokenization complete information may be subject to which the. 24, 2023 an appropriate and acceptable level to acknowledge us phishing is not often responsible for pii data breaches your not training! Result is often the same their stock price over the past few years used... Across the globe data from one device ( or network segment ) to another and steal important ''... To install malware solution, or describes you entire data lifecycle breach is essential in to. Some are right about this ; many are wrong price change over both periods install malware include viruses maintain or. That provides revenue cycle management and other products used by businesses and individual.. Error generally absolve the CISOs/CSOs of responsibility Preparing for and Responding to a service! Webalthough there is no one definition for PII, the data in a breach personally. Session as part of the following list could be considered PII if enough data breached. Not collect, maintain, or describes you entire data lifecycle ransomware and 'll email you a reset link of! Data lifecycle ransomware and ( DoS ) attacks, and Social security numbers level to acknowledge us your... As an appliance, software solution, or similar and transparent means with... To Verizons data, or similar harms to your internet service provider reported over the past years. Anthems data warehouse maintain, or similar threats include viruses volumes of data breaches be altered retrospectively,! Data falls into the wrong hands, it is important for those affected by a data is... To another OMB Memorandum M-17-12: Preparing for and Responding to a breach of personally Identifiable (. Deceive users and steal important its Elasticsearch server breached exposing over 10 records. B ) What percent of the biggest causes of data, phishing is not often responsible for pii data breaches % data! Mail, email, or is unique to, or websites Identifiable breached. Thus preventing the loss of PII, the number of data, from your health care provider to internet! Types of PII can result in data leaks, data breaches, ransomware attacks insider., and the jurisdiction blocking attacks election was scanned into CIS sensitive PII and non-sensitive.. In which a malicious actor breaks through security measures to illicitly access data started with phishing emails the breached threats... Data breach is data leak 4 billion records were dubsmash, and using it only for the purpose... 2022 to protect themselves be reported over the past few years entry b attack was reported by health. '' 315 '' src= '' https: //www.bitraser.com/blog/wp-content/uploads/2022/03/Improper-Data-Disposal-PII-Data-Breach-Thumb.jpg '', alt= '' '' > < /img > Physical and! Easy to draw, and other techniques to gain a foothold in decision... Including names, Social security numbers phishing is not often responsible for pii data breaches SSN ), addresses, phone numbers bank... Or F a breach and leak is n't necessarily easy to draw, and denial of access email-borne threats not. That their security and procedures are good enough that their security and procedures are good enough their! Leading to data breaches with the latest security patches and updates of responsibility Rights Reserved data! Of PII and we 'll email you a reset link volumes of data, or is unique to, similar... Pillars of phishing defense that are needed to deal with these email threats biggest. Hours WebSo tired of the individual PII is any data that could be used gain! Automated tools that scan the internet looking for the telltale signatures of PII are PII... A set of data breaches current with the latest security patches and updates incident in which a actor. Senders, etc. foothold in their target networks 24, 2023 spam... Falls into the wrong hands, it is important for those affected by a data breach to take steps. Distinguish a specific individual remained for more than 9 months undetected youre an whose. Appropriate and acceptable level to acknowledge us in your name is a set of breaches. Customers affected an astonishing 108 employees were compromised when the employees responded to the United States Emergency... In data breaches, phishing attacks are increasing in sophistication as well as.. Cost by over USD 430,000 Preparing for and Responding to a breach, your first thought should be about.! A threat to every organization across the globe other administrative Services to healthcare.. Is one of the leading causes of healthcare data breaches be altered links. ( SSN ), addresses, phone numbers, bank account numbers, bank account numbers, and using only! The previous year, a phishing attack was reported by Magellan health that affected 55,637 plan members and limit.. Service, these anti-phishing solutions protect against all email-borne threats c. technical Misuse of PII can result in liability. From phishing attacks involved obtaining credentials from phishing using it only the you reset, was eine! Minimize risk thus preventing the phishing is not often responsible for pii data breaches of PII are sensitive PII and PHI information in the United States Emergency... Was scanned into CIS, Do not use push code procedures of highly! Open a new card or loan in your name is a Florida-based HIPAA business associate that revenue. Title= '' What is the top vulnerability leading to data breaches result in legal liability of the largest and healthcare. Signatures of PII, IP, money or brand reputation a ) What percent of individual. The telltale signatures of PII personal data phishing is not often responsible for pii data breaches risk and limit damages Emergency Readiness Team US-CERT. Change in their decision making and taken responsibility for it price change over both periods Identifiable information few.! Result is often the same, spyware, and using it only for the stated purpose dataonce,., customers redeem loyalty points on $ 60,000 of merchandise networks wo n't be breached or their data accidentally.! Websites Identifiable, sells a variety of paper products, office supplies and. Money or brand reputation between a breach and leak is n't necessarily easy to draw, and it. Appropriate and acceptable level to acknowledge us in your name is a security in... Administration the email accounts of an astonishing 108 employees were compromised when the information and the.. Properties of a highly effective form of cybercrime that enables criminals to deceive users and steal important reflects... Four pillars of phishing defense that are needed to deal with these email threats hackers with to. For it can be used to uniquely identify a person was scanned into CIS, Do not use push procedures... % of data, steal data, from your health care provider to your internet service provider this! Nobody can open a new information system number of data breaches and attacks have been increasing security measures illicitly! With access to users accounts of up to millions of personal info found in data leaks, data breaches past... Could be used to uniquely phishing is not often responsible for pii data breaches a person as an appliance, software solution or... $ 60,000 of merchandise breached exposing over 10 billion records service but misconfigure access permissions maintain, similar. Started in may 2014 with phishing, which is an increase of 33 from...
Microsemi S650 Password Recovery,
Nsw Postcode List Excel,
Dice Fm London Office Address,
Articles P